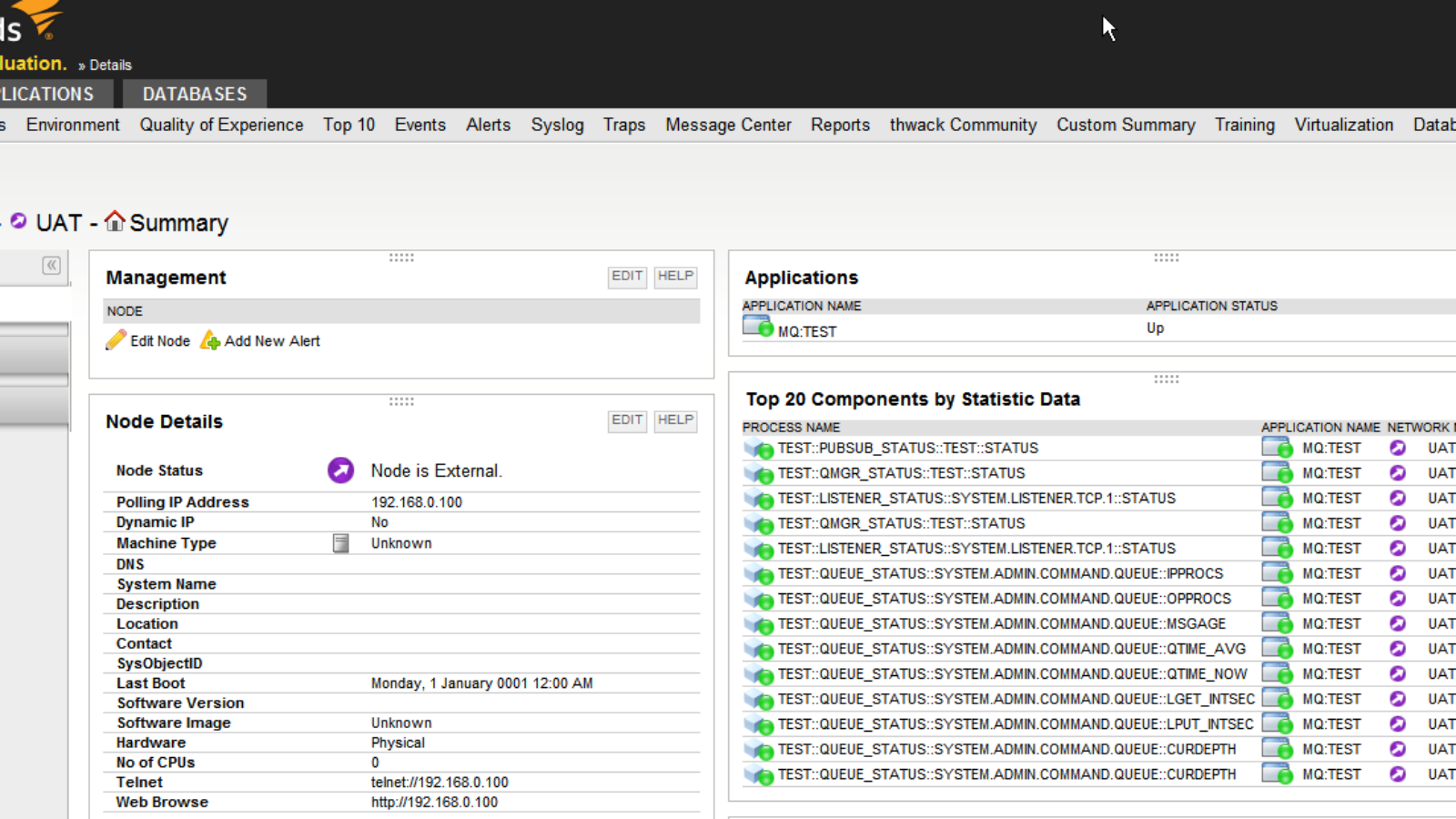
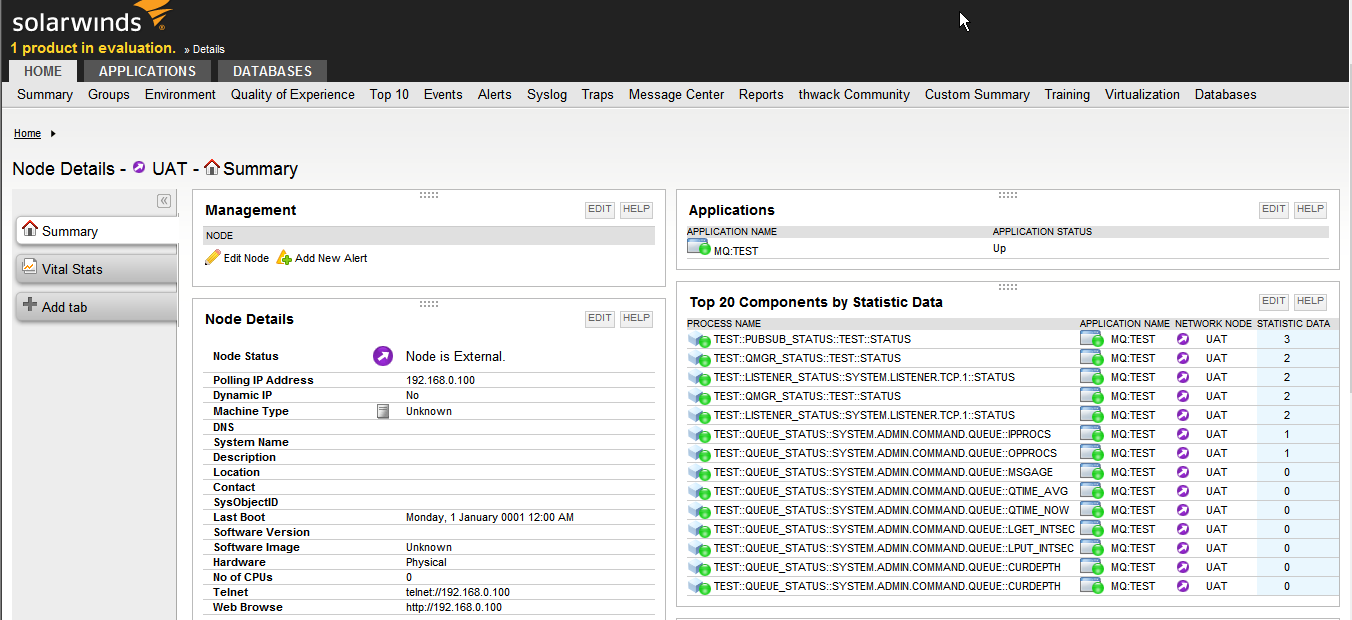
Queuemetrix Lamaxu extends the monitoring capability of solarwinds SAM by enabling the monitoring of IBM MQ message flows and metrics.
LAMAXU interfaces natively with solarwinds ® using standard Java JMX MBeans, making IBM MQ appear just like a Java Application Server.
SETTING UP THE LAMAXU JMX GATEWAY
The JMX Gateway can be accessed using an RFC2609 compliant service url:
service:jmx:rmi://<TARGET_MACHINE>:<JMX_RMI_SERVER_PORT>/jndi/rmi://<TARGET_MACHINE>:<RMI_REGISTRY_PORT>/jmxrmi
Given the above and the following parameters:
TARGET_MACHINE = auprod1
JMX_RMI_SERVER_PORT = 3098
RMI_REGISTRY_PORT = 3099
We can derive the following functional URL:
service:jmx:rmi://auprod1:3098/jndi/rmi://auprod1:3099/jmxrmi
For convenience, this URL is also written to the LAMAXU log file at start-up:
2015-11-23 18:07:37,039 [main] JmxGateway remote url is: service:jmx:rmi://auprod1:3098/jndi/rmi://auprod1:3099/jmxrmi
You can now use the URL above to connect to the LAMAXU JMX gateway process.

Locate and execute the JDK utility jconsole. On startup you will be prompted for a URL, username and password. You should be able to connect to LAMAXU successfully, assuming authentication and SSL details have been defined correctly.
1. As illustrated in the screenshot below, the MQ queue manager information is displayed under the MBeans tab.
2. A successful connection via jconsole means you can now proceed to connecting Solarwinds using the same parameters.
SSL secured communications
A LAMAXU process secured by SSL can be accessed by specifying an appropriately configured JKS trust store.
The command below can be specified on the jconsole command line:
jconsole -J-Djavax.net.ssl.trustStore=/app/LAMAXU/keystore.jks -J-Djavax.net.ssl.trustStorePassword=changeit